Last Updated: May 2025
With SaaS adoption accelerating across industries, so do the risks. Studies show that nearly 82% of companies have experienced unauthorized SaaS usage, known as shadow IT. Additionally, over 40% of data breaches are now linked to misconfigured SaaS applications.
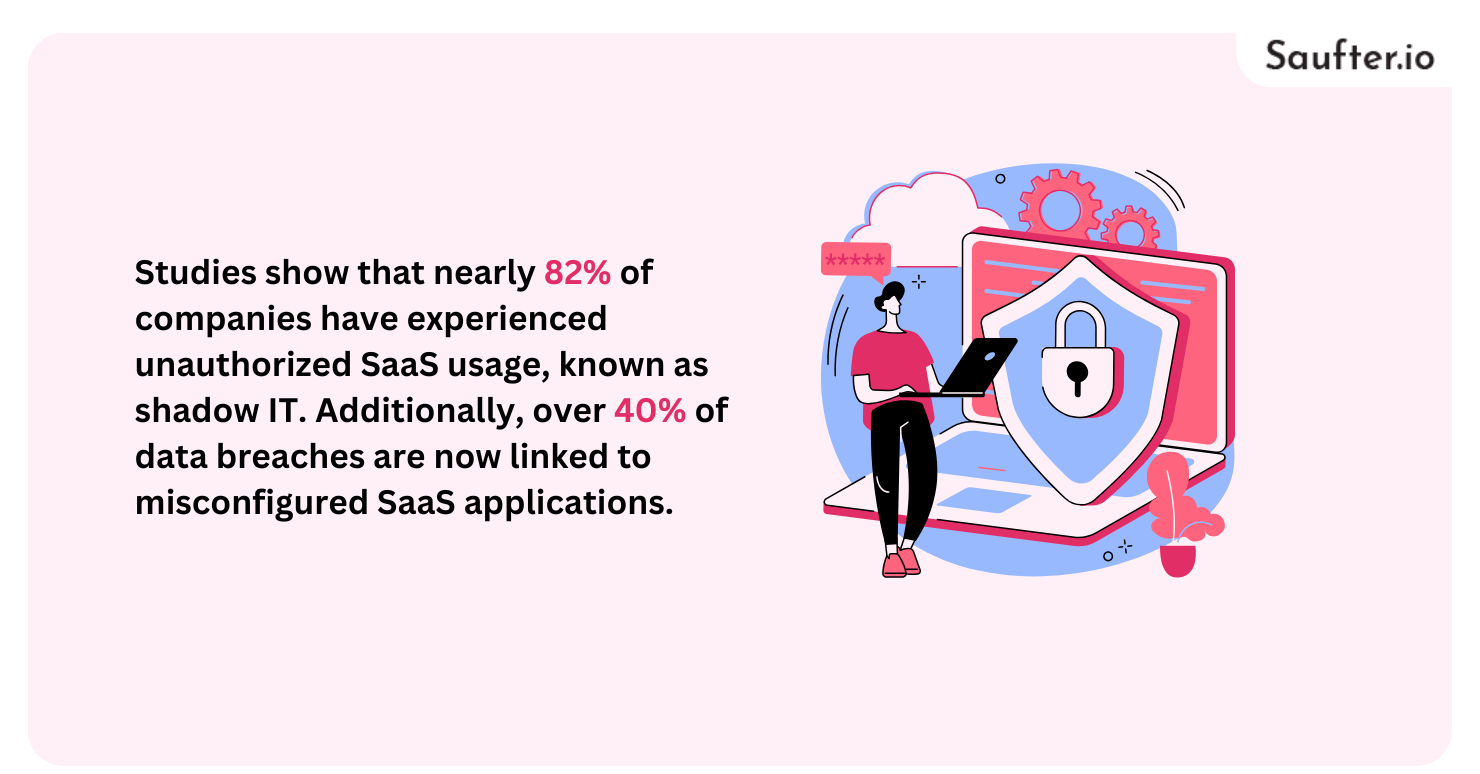
This is why SaaS security posture management tools are no longer a luxury, they’re a necessity. These platforms offer visibility, threat monitoring, policy enforcement, and risk mitigation, helping businesses secure their growing SaaS ecosystems.
This blog explores the top 11 SaaS security posture management tools you should consider in 2025. Each tool provides a unique set of features that help organizations protect sensitive data, stay compliant, and reduce security blind spots.
What Are SaaS Security Posture Management Tools?
SaaS security posture management tools help organizations detect, assess, and manage risks related to the use of SaaS applications. They continuously monitor user activity, data sharing, configuration settings, and third-party integrations. These tools are designed to:
- Discover unsanctioned or unmanaged apps
- Identify misconfigurations and compliance gaps
- Enforce security policies across cloud services
- Prevent data leaks and unauthorized access
As SaaS sprawl continues, traditional endpoint protection or network monitoring alone isn’t enough. SSPM platforms fill this visibility and control gap.
Key Benefits of Using SSPM Tools
- Centralized Visibility: Get a full picture of all SaaS applications in use, including shadow IT.
- Risk Scoring: Prioritize threats based on real-time insights and usage behavior.
- Compliance Automation: Maintain continuous compliance with standards like GDPR, HIPAA, and SOC 2.
- Automated Alerts: Respond to threats before they escalate with automated workflows.
- Security Policy Enforcement: Define and apply organization-wide SaaS usage policies.
Top 11 SaaS Security Posture Management Tools in 2025
1. Zluri
Rating: 4.8/5
Zluri’s discovery engine identifies all SaaS apps in use, even those bypassing IT approval. Its dashboard segments applications by risk, compliance status, and access level. The platform integrates with your SSO and identity providers for enriched visibility.
Key Features:
- 9-layer SaaS discovery method
- Risk and threat scoring for each app
- Real-time compliance tracking (GDPR, SOC 2, etc.)
- Encrypted data storage with retention control
- Alerts for risky or unused SaaS apps
Why it stands out: Powerful threat scores, detailed compliance tracking (e.g., GDPR, SOC 2), and proactive alerts for risky SaaS usage.
2. Zscaler
Rating: 4.3/5
Zscaler extends its zero-trust architecture into SSPM. It enables fine-tuned access policies and detects shadow SaaS usage. Zscaler’s unified platform supports dynamic policy enforcement and real-time monitoring.
Key Features:
- Dynamic policy enforcement
- SaaS usage discovery and shadow IT detection
- Integration with secure web gateways
- Real-time visibility across apps
Why it stands out: Excellent integration with enterprise networks and secure web gateways.
3. Varonis
Rating: 4.5/5
Varonis helps enterprises secure SaaS data through granular permission tracking and behavioral analytics. It detects anomalies, improper access, and lateral movement risks in real time.
Key Features:
- Real-time threat detection
- Fine-grained permission management
- User behavior analytics
- Compliance reports and audit trails
Why it stands out: Best for large enterprises with complex data structures and stringent compliance needs.
4. Obsidian Security
Rating: 2.5/5
Obsidian combines user behavior analytics with continuous posture monitoring. It centralizes identity and access insights across multiple SaaS platforms.
Key Features:
- Unified security posture dashboard
- Continuous threat detection
- Role-based access insights
- Behavioral anomaly detection
Why it stands out: Great for organizations needing fast deployment and high-fidelity user activity insights.
5. Adaptive Shield
Rating: 4.8/5
Adaptive Shield automates SaaS security assessments and compliance workflows. It provides real-time misconfiguration alerts and tracks user behavior to detect threats.
Key Features:
- Real-time risk scoring
- Compliance automation tools
- Custom security policies
- Automated remediation and alerts
Why it stands out: Excellent at supporting compliance and automating remediation tasks.
6. Spin.AI
Rating: 4.8/5
Spin.AI focuses on SaaS access management, insider threat detection, and backup. It’s built to handle identity governance for platforms like Google Workspace and Microsoft 365.
Key Features:
- Privileged access management
- Real-time monitoring of user activities
- Seamless integration with major SaaS apps
- Automated backups and data protection
Why it stands out: It combines SSPM and backup in one solution.
7. AppOmni
Rating: 5/5
AppOmni offers in-depth insights into app configurations, data access paths, and external integrations. Its threat intelligence engine automatically flags risky behaviors.
Key Features:
- Visibility into user permissions and SaaS data flow
- Continuous security checks and alerts
- Integration with platforms like Salesforce and Slack
- Detailed reporting and remediation guidance
Why it stands out: 360-degree view into SaaS data flows and permission levels.
8. Axonius
Rating: 4.0/5
Axonius focuses on device and app inventory management, linking asset data to security insights. It tracks all endpoints and their SaaS access to mitigate exposure.
Key Features:
- Asset inventory across devices and SaaS apps
- Policy enforcement engine
- Real-time compliance monitoring
- Integrates with over 500 tools
Why it stands out: Device-first security model for SaaS environments.
9. Cynet

Rating: 4.2/5
Cynet integrates SSPM with endpoint detection and response (EDR). It enables unified control of SaaS access and threat prevention through automation.
Key Features:
- Unified dashboard for endpoint and SaaS security
- Threat intelligence integration
- Automated incident response workflows
- Real-time access monitoring
Why it stands out: Best for organizations wanting a combined EDR + SSPM experience.
10. DoControl
Rating: 4.6/5
DoControl’s policy engine allows granular control of who can access, share, and modify SaaS data. It also provides real-time alerts and integrates well with collaboration tools.
Key Features:
- Granular data access policies
- Real-time alerts for suspicious activity
- Automated compliance enforcement
- Integration with file-sharing tools
Why it stands out: Ideal for mid-size companies focused on access governance.
11. Saasment
Rating: 5/5
Saasment emphasizes role-based access control (RBAC), compliance assurance, and seamless integration with identity providers. It’s great for small teams scaling their SaaS stack securely.
Key Features:
- RBAC-based access policies
- Real-time monitoring of user activities
- Compliance dashboards and audit trails
- Integrations with SSO and IAM tools
Why it stands out: Intuitive UI, fast deployment, and strong audit trails.
SaaS Security Best Practices
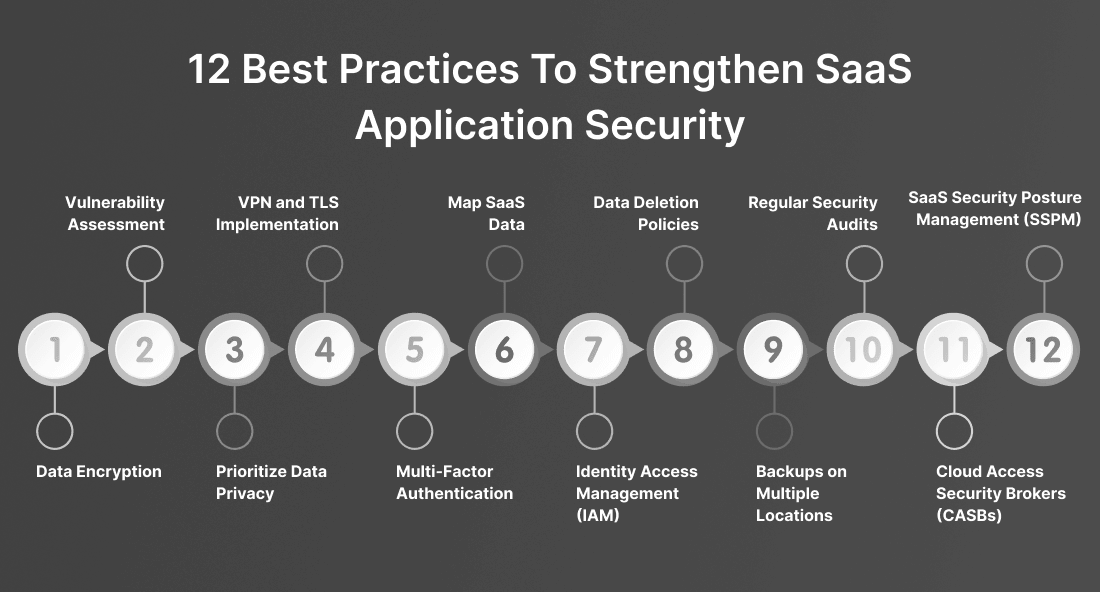
When implementing SaaS security, one must be very careful not to be reactive but proactive. It is important to make sure that the organization uses security that is layered security, and at the same time, clear policies must be implemented to be able to avoid vulnerabilities and misconfigurations.
One of the methods considered a security best practice is the implementation of a single sign-on process that is complemented by multi-factor authentication for all SaaS tools. Among other things, such a measure is capable of preventing unauthorized access, even if the credentials are leaked.
Furthermore, one of the most substantial steps is the SaaS application inventory and access audits. IT teams need to keep the latest list of all the SaaS apps in use and periodically review user access rights. As a case in point, this will involve not only shadow IT but also apps that are taken advantage of without the approval of the IT department and create security blind spots.
Utilizing the encryption of both data at rest and in transit is also a great example of this best practice. Through encryption, the sensitive data stays safe even if it falls into the wrong hands. Moreover, organizations have to implement role-based access control (RBAC) to make sure that the employees are given access only to the necessary data for their duties.
Periodical training of the employees is necessary to ensure that security awareness of the employees is well-coordinated. Most of the security incidents start with phishing or accidental sharing of sensitive files. Educating teams on the identification of threats and practicing safe file-sharing habits can minimize these risks.
Additionally, integrate automated tools to monitor and flag risky user behavior or misconfigurations. Platforms that provide real-time alerts and remediation workflows can significantly reduce time-to-response and avoid breaches.
Finally, keeping a SaaS security incident response plan ready ensures a rapid and coordinated approach to handling any incident. These practices collectively contribute to building a strong and resilient SaaS security foundation.
SaaS Security Posture Management Vendors

Choosing the right SSPM vendor goes beyond selecting based on brand recognition. Businesses should evaluate SaaS security posture control capabilities in line with their current environment and scalability needs. Not all vendors provide the same depth of analysis, automation, or integration.
A strong SSPM vendor will offer continuous monitoring, detailed risk scoring, and granular visibility into user permissions, data flows, and configurations. Additionally, their platform should provide actionable insights and policy enforcement tools that align with your security governance structure.
When comparing SaaS security posture control solutions, check for robust integration with identity providers (like Okta or Azure AD) and the ability to monitor third-party app connections. These integrations allow for broader oversight of access points and reduce vulnerabilities.
Also, look at the interface that is intuitive. If the dashboard is it too complicated, it will lower the acceptance, and this, in turn, will be beneficial to the users as they will be able to utilize the tool to their best advantage. A good vendor of SSPM will also ensure that their customers are satisfied with their service, have complete documentation, and receive assistance during the process of knowledge transfer (onboarding).
Automation is yet another important matter. The best providers have automated workflows of the resolution of events, alerts, and compliance checks that reduce the additional hands-on effort significantly. The automation even frees the security team to concentrate on the big picture rather than being wasted by the routine stuff.
Finally, pricing and licensing flexibility matter. Ensure the vendor’s pricing model matches your usage patterns and anticipated growth. Opt for vendors who offer transparent pricing and allow you to scale easily.
With the right SaaS security posture control vendor, your organization will be better positioned to prevent breaches, maintain compliance, and respond swiftly to any anomalies.
Let us now introduce you to the best SaaS AI-based Email marketing tool- Saufter.io
Saufter: The Best SaaS Email Marketing Tool

In today’s fast-moving digital landscape, Saufter AI emerges as a game-changing email marketing solution, especially for SaaS businesses, e-commerce platforms, and online brands. Powered by advanced artificial intelligence, Saufter helps you streamline your campaigns, boost engagement, and increase conversions through smart automation and data-backed strategies.
Key Features
- Competitor Email Tracking: Automatically monitors and analyzes your competitors’ email campaigns, helping you stay ahead of the curve.
- User Behavior Analysis: Studies user interactions on your website and tracks their journey to generate targeted campaign suggestions.
- Personalized Email Campaigns: AI-driven personalization enhances email deliverability and engagement, ensuring your messages reach the right audience.
- Cohort-Based Suggestions: Segment users based on their engagement levels and behaviors to optimize campaign effectiveness.
Conclusion

With the average enterprise using over 130 SaaS apps, visibility and control are more critical than ever. Investing in the right SaaS security posture management tools is no longer optional, it’s essential for safeguarding data, reducing risk, and meeting compliance.
Choose a tool based on your organization’s size, regulatory obligations, and integration needs. Be sure to consider features like automated alerts, access visibility, and compliance readiness.
By 2026, companies that actively monitor their SaaS posture with SSPM solutions are expected to reduce security incidents by up to 60%. So, now is the time to adopt the right SaaS security posture management tools and future-proof your cloud security strategy.

















